Enable Advanced Cyber Defense Programs
Secure your systems, network, and programs from innovative digital attacks.

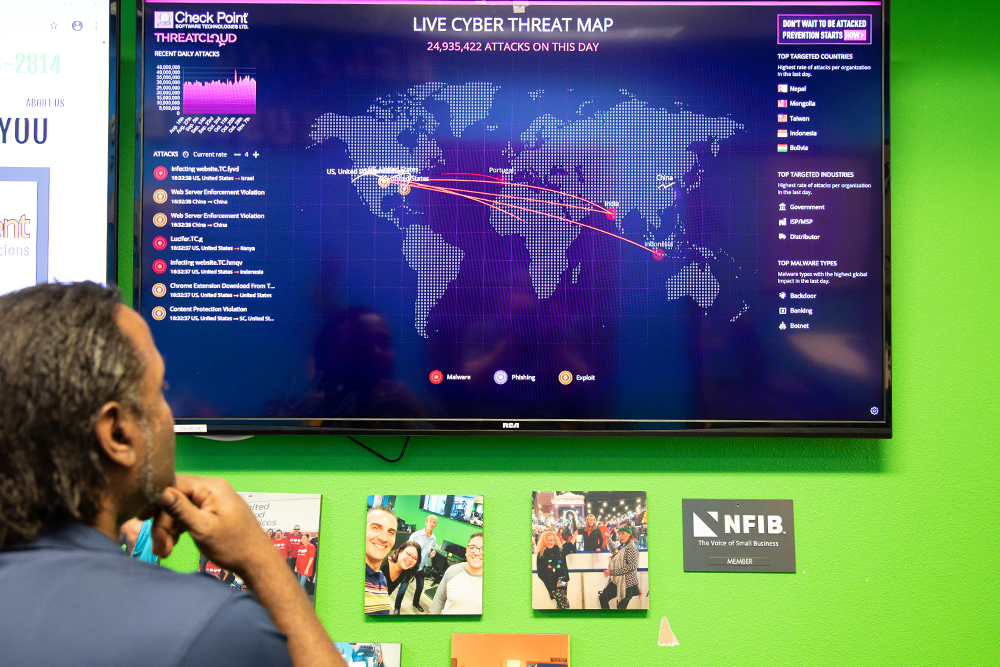
Cyber crime is growing exponentially and the risks are greater than ever before. Build a robust Cybersecurity Program and establish Cyber Resilience with ITS' dedicated team of cyber professionals.
Schedule your Evaluation
Review your Cyber Program
Start protecting your business
Schedule a friendly cybersecurity evaluation

Review your Cyber Program - Plan and Roadmap

Take the initial steps to implement your cybersecurity program to increase your security posture.

Give your team the freedom to concentrate on their company's most important goals. We provide service in all the following areas, and more, to let your people fully devote themselves to your mission.
Secure your systems, network, and programs from innovative digital attacks.
Be continuously in compliance with the latest federal, defense, and industry security regulations.
Mitigate risks by adopting Next-Gen cybersecurity best practices

Cybersecurity is the process of protecting your networks, systems, devices, and programs from cyber-attacks. In a nutshell, Cybersecurity is your organization’s way of protecting the company, employees, and customers from the plots that hackers are trying to implement.
The type of data can vary by the hacker, and by cyber-attack, however, hackers are typically after data that they can make money off of or leverage in other attacks. A few examples of data that hackers may be interested in are:
• Customer information including both personal and company level details
• Users of your software, and their account information
• Credit and debit card information
• Bank account information of organizations and individuals
• Employee information including social security numbers, driver’s license numbers, birth dates, addresses, and medical details
Benefits are often viewed as tangible elements. The benefits of a strong Cybersecurity program, however, are intangible. Cybersecurity is all about prevention – stopping a hacker from accessing company, customer, and employee data. And this prevention equals a level of protection for your networks and data. It also means peace of mind for your employees and customers because they are confident that the data and information that they have shared with your organization is safe. And, let’s face it, some of that data is valuable – credit card information, social security information, medical information, billing information, and access to products are just a few examples. That prevention also equates to confidence in your business from customers, employees, and stakeholders. And, lastly, it means that if a cyber attack were to occur, your organization is prepared to swiftly handle the situation and minimize the impact.
Yes! In fact, approximately 58% of data breaches happen to small businesses. And, two-thirds of SMB’s have suffered a cyberattack within the past 12 months! Why? Because hackers look for the path of least resistance, the easy route. And small businesses that have the “it won’t happen to me” thought are a dream for hackers. Even those small businesses that have anti-virus software are at risk. One report indicated that 82% of those attacked said that malware was able to get through their anti-virus software. The bottom line is that no business, large or small, should consider themselves safe. Take the proper precautions and implement a Cybersecurity program for your organization.
Thieves steal and sell databases, credit card information, financial transactions, leaked emails, user logins and credentials, and company secrets that can financially harm your business. They profit after committing theft through phishing attacks or by using compromised employee login credentials.
They use the Dark Web to do this.
Dark web monitoring is an identity theft prevention product that lets you monitor your confidential business information on the Dark Web and receive notifications if it’s found online.
You’ll be in control of the information you want to be monitored. You’ll receive alerts via email if any of this information is found on the Dark Web. Your service will let you know any next steps you should take if this happens.
CMMC is required for businesses interested in bidding on government contracts. CMMC is designed to protect two specific kinds of information:
After CMMC goes into effect in Fall 2020, all businesses contracting with the DoD will be required to have certification to a certain level depending on the nature of their contract. Level 1 is equivalent to FAR 52.204–21, so businesses that have already achieved this standard independently will have a head start on those just beginning the process.
"I think to not adopt some form of advanced security these days would be incredibly foolish. The biggest benefit ITS provides is the weight off my shoulders knowing that they're involved and we've prepared ourselves as best as we could for any cyberthreats. That's the most important to us."
JP Halverson | VP of McQuarrie Associates

"ITS helped us implement a layered security model addressing both our immediate needs and long-term goals. Our executive team sleeps better at night, and our remote staff can work security and efficiently. With ITS as our partner, we're confident that we can fulfill our mission securely and efficiently."
Sarahvon Buenavista | Director of IT Operations

“I’m working with startups but also very large companies—some of the largest ones in the world. So the security of data and confidentiality is foremost. When I was approached by ITS about a conversion to a new cybersecurity system, it made absolute sense to me. Now that we’ve going through the cybersecurity upgrade, it gives me and my clients complete peace of mind knowing that everything is secure.”
Mary B., Owner | Mary Bordeaux Consulting

"What you don't want is someone from another country shutting you down and taking all of your money, because this is our livelihood. You are keeping us secure so we can sleep at night and help us make sure all of our 600+ employees have a job tomorrow."
Tully W., Fixed Operations Director | The Niello Company

"I felt good about our relationship when we started in 2021 and I feel even better about it now. The amount of resources that you have. The support that we get. I think it's fantastic. I have ITS on my side. It inspired a lot of confidence in me to have that to fall back on and to move forward with."
Matt Ryan | The Niello Company

"I've been working with ITS for close to eight years now, and it's just been a great partnership. It's only been a fantastic and beneficial partnership for the San Francisco Association of REALTORS."
Jay Pepper Martens | San Francisco Association of Realtors

"The technician did a great job and was thorough. The issue was fixed and ITS double-checked some background settings to verify those were correct and make sure there were no hacks or viruses (computer illnesses) from unwelcome emails. THANK YOU!"
Michele G. | Rowpar Pharmaceuticals
"The technician did a great job. The likely culprit was ascertained and that fixed both the Desktop & Laptop issue I was experiencing. MFA working as well as remote desktop so I am a happy customer!"
Mike D. | CFO, Fort Mojave Indian Tribe
Read stories from real clients who share the same frustrations and are now enjoying cybersecurity.
Schedule a meeting with one of our cybersecurity experts to learn about your specific needs and create your custom plan.

Schedule a meeting with one of our cybersecurity experts to learn about your specific needs and create your custom plan.